Cloud Computing Icon Over The Network Connection, Cyber Security Data Protection Business Technology Privacy Concept. Stock Photo, Picture And Royalty Free Image. Image 124346671.

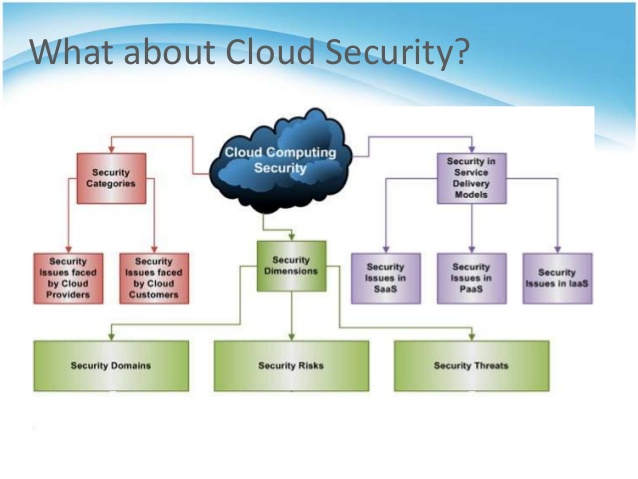
Cloud Computing Security How Does Cloud Security Work Ppt Introduction | Presentation Graphics | Presentation PowerPoint Example | Slide Templates